- Home
- :
- All Communities
- :
- Products
- :
- ArcGIS Enterprise
- :
- ArcGIS Enterprise Questions
- :
- Re: Enterprise Infrastructure with 2 Network Load ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Enterprise Infrastructure with 2 Network Load Balancers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
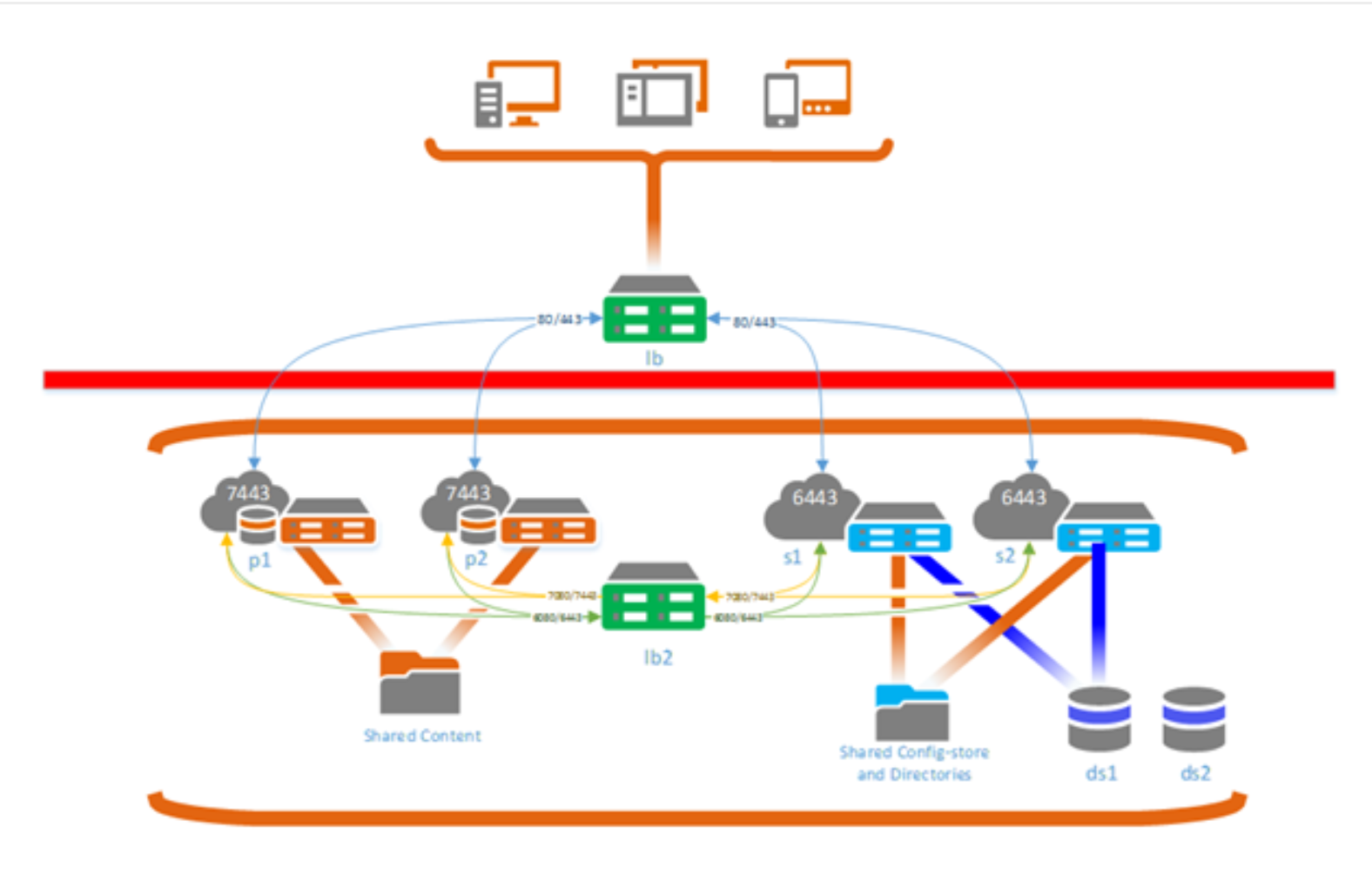
In the below example, which is a snipit taken from ESRI documentation found here, Deployment scenarios for a highly available ArcGIS Enterprise—Portal for ArcGIS (10.6) | ArcGIS Ente... , I am curious about the difference between internal and external requests.
In the example, would clients who are behind the firewall on the internal network, have to "go out" to "get back in"? Does the DMZ Load Balancer handle ALL traffic, or just any external requests. So internal employees would access the Portal via https://internalNLB.Internaldomain.com/arcgis/content and external access (authenticated field users) would access the portal via https://externalsNLB.externaldomain.com/arcgis/content.
If it is the case where internal points to the internal NLB and external to the external NLB, can you have Active Directory Federated Services on both NLB without any authentication issues? I thought with Portal, only one machine will handle security.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
I'll respond to your question on that other post here. Portal can only have one user-facing URL, (so either externallb.domain.com or internallb.domain.com). You can try to set up DNS so that public users reach the external LB through lb.domain.com, which forwards traffic to the portal, and internal users users reach the internal LB through the same URL, lb.domain.com, which forwards traffic to the same portal. You would need to sort out how to send requests that originated externally are sent back to the external LB, and the same for the internal LB. Perhaps you can do this with some sort of header or cookie and something in front of the portal to handle that for you, but I'm not sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
Thanks Jonathan, I think we will be able to make it work by assigning rules on our firewall.
The LB in the DMZ is NAT'd so it will have an external IP and an internal IP.
If someone from our internal network tries to access our portal, when the request hits the firewall, the rule will recognize the ip they are coming from and automagically route them to the internal IP of the DMZ Load Balancer, by-passing the need to go "out" to the external IP of the LB. And all external requests, will obviously just hit the external IP of the DMZ LB and funnel traffic as normal.
I'm no networking or firewall expert, but I believe this is the solution (I've wracked my head over this for awhile haha)
What do you think?