- Home
- :
- All Communities
- :
- Developers
- :
- JavaScript Maps SDK
- :
- JavaScript Maps SDK Questions
- :
- Application-level token authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
I'm looking to narrow availability of some map services utilized by my JSAPI application. I am using ArcGIS Server 10.3 on a local Windows/IIS install with proxy availability.
I have several applications on different domains and servers accessing the centrally-located ArcGIS Server resources, which are publicly available... I'd like to have it set-up so that only these applications can access the resources, but users shouldn't need to supply credentials - the idea is to make it difficult for a user to inspect the web requests to acquire the public resources outside of the application and poke around for data harvesting and hot-linking in non-sanctioned applications.
What's the best way to accomplish this? I've found several resources and write-ups on the topic, but I am still unclear as how to do this correctly and securely.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
To access ArcGIS secured services through proxy without prompting for credentials. In the proxy.config add the <serverUrl> with credentials
<serverUrl url="https://yourGISServer.domain/arcgis/rest/services/"
matchAll="true"
username="siteadmin"
password="siteadmin"/>
Note: When doing this its important to set the allowedReferers property as well to limit the access to the proxy itself.
These are the esri proxy configurations mentioned on github:
- allowedReferers="http://server.com/app1,http://server.com/app2" : A comma-separated list of referer URLs. Only requests coming from referers in the list will be proxied. See https://github.com/Esri/resource-proxy/issues/282for detailed usage.
- username: Username to use when requesting a token - if needed for ArcGIS Server token based authentication.
- password: Password to use when requesting a token - if needed for ArcGIS Server token based authentication.
Thanks,
-Girish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
Hey Chris,
Here are couple of suggestions:
Using esri proxy:
1. Secure services on ArcGIS server.
2. Next is to set up esri proxy. As I understood, you have several applications accessing this secured service resource. therefore:
A. If all these apps are in one web server then publish esri proxy once on the web server OR
B. If the apps are in different servers then publish esri proxy on each separate web server.
3. Configure proxy so that the secured service is only accessible through these apps. To do that specify the URL for the apps in "allowedReferers" parameter of proxy config. This is a comma separated list of application urls that can make call to this proxy. The call to the proxy will be allowed only if its made from within the specified apps. Any calls made from unspecified app or directly from browser will be blocked.
4. In the proxy config specify the username and password for the secured arcgis services. So that the user need not to provide any credentials. the proxy will take care of generating and managing the token to access secured services.
Using ArcGIS Online:
1. Secure Map service on ArcGIS server.
2. Add it into AGOL as ArcGIS Server Web Service.
3. provide required credentials
4. select the option to save the credentials if you want registered apps to use Application level authentication automatically and not ask for credentials. Dont save credentials if you want user to enter it each time this resource is accessed. When you publish this layer its private and other users cant access it.
5. register you apps in AGOL and use identityManager in the apps to perform Application level authentication.
here are few useful helo items for this approach
ArcGIS Server web services—ArcGIS Online Help | ArcGIS
Implementing Application Authentication | ArcGIS for Developers
Hopefully this will help.
-Girish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
Thanks,
I remember seeing something relating to secure services when initially installing and configuring the proxy. Right now, it's open-ended access, which really isn't a problem (yet, at least). The proxy is published on each application server now... I'll look more into this.
Regarding AGOL, I saw that it seemed pretty easy to set-up, relatively, but, we unfortunately can't go this route due to policies and architecture - but good info to know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
More specifically, this part from your suggestions:
4. In the proxy config specify the username and password for the secured arcgis services. So that the user need not to provide any credentials. the proxy will take care of generating and managing the token to access secured services.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
To access ArcGIS secured services through proxy without prompting for credentials. In the proxy.config add the <serverUrl> with credentials
<serverUrl url="https://yourGISServer.domain/arcgis/rest/services/"
matchAll="true"
username="siteadmin"
password="siteadmin"/>
Note: When doing this its important to set the allowedReferers property as well to limit the access to the proxy itself.
These are the esri proxy configurations mentioned on github:
- allowedReferers="http://server.com/app1,http://server.com/app2" : A comma-separated list of referer URLs. Only requests coming from referers in the list will be proxied. See https://github.com/Esri/resource-proxy/issues/282for detailed usage.
- username: Username to use when requesting a token - if needed for ArcGIS Server token based authentication.
- password: Password to use when requesting a token - if needed for ArcGIS Server token based authentication.
Thanks,
-Girish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
I completely agree with Girish's comment. If you do not specify an allowedReferers, it's not just your ESRI / AGS servers that you leave open for all to see and use. Someone can actually use that proxy file to get to other servers in your network. We tested this recently and was shocked to see that we were impacting other servers on our network by leaving it just with the wildcard.
The documentation says 'you shouldn't leave allowedReferers as the default *. The documentation should be much more strongly worded that this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
I wasn't aware of this issue - we haven't had any crop-up with penetration scans... We understood that our services were open for all, provided users weren't blocked by firewall, but that was ok since they were services not needing to be secure. Now, we need secure services - it's been so long since I've had to set-up/configure anything proxy-related!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
That was the scary part for us. We have extensive cyber security scans that are run on our servers. These did not turn up the problem. It was just some internal testing of how tight to make our GIS proxy configuration, and we were testing with non-ESRI services to see what we could see. More than we thought we should be able to!
I'm sure every server environment is different. It could just be the combination of our settings, network and security that were specific to us. I couldn't even begin to describe ours, its not my subject area and we're a large organization.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
Everyone, thanks for the help - I think this is working well! In Chrome at least... In IE, I'm having an issue and am receiving an authentication log-in when attempting to access the service:
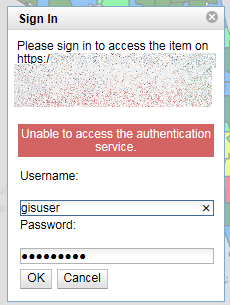
I'm looking into it now and ran across this technical article:
42332 - Unable to access the authentication service
Which is not particularly conclusive in my case - the SSL certs are valid and confirmed on the GIS server. I can authenticate through REST when directly accessing through the web; I have also verified token generation using http://gisserver.domain.com:6080/arcgis/tokens
I'm thinking it might be the way IE is handling my localhost dev app - it's currently using a self-signed cert, which may be breaking the chain, at least in IE? Seems like it may be according to some info in &amp;quot;Unable to access the authentication service&amp;quot; while trying to add secured ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
Seems Chrome must have had some cached JS - it doesn't work here, either. I'm pushing it to dev now to see if it's the self-signed cert on my local build.