- Home
- :
- All Communities
- :
- Products
- :
- ArcGIS Online
- :
- ArcGIS Online Questions
- :
- Access Organization Resource Programmatically Open...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Access Organization Resource Programmatically OpenID Connect Credentials
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
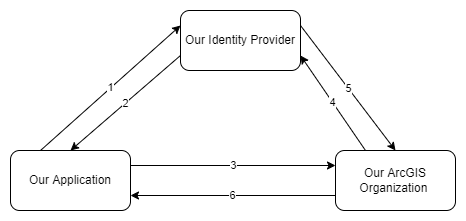
We have set up the ability for users to sign in to ArcGIS online via our Identity Provider using OpenID Connect and OAuth 2.0 as described by this documentation. This is working well. Now the question is how can we pass the token for our authorized user to ArcGIS to access a protected resource such as a FeatureLayer? To clarify, theArcGIS Online member of our Organization is authenticated via OpenID Connect and, in the same way that this user can access ArcGIS Online, we want him/her to be able to access a resource from our Organization from our app. How can this be accomplished or can someone point us in the direction of some documentation for this? Following is the expected flow:
- From our application, a user requests and access token from the Identity Provider built on IdentityServer4 (using OpenID Connect and OAuth 2.0) [this is already done]
- The Identity Provider authenticates the user and returns an access token [done]
- From our app, a user attempts to load a map using a FeatureLayer belonging to our Organization, which triggers a resource request (we are using @arcgis/core, see technical details in the code below) for that FeatureLayer to our ArcGIS Organization, passing our access token [how to pass our token in this case?]
- ArcGIS sees that this token it contains the user ID for the aforementioned user in their system, which it knows is matched with the OpenID "Authority" (specified by the setup described in the link above), so ArcGIS verifies this token with the OpenID "Authority"
- Our Identity Provider responds that the token is valid
- ArcGIS trusts the user and returns the resource
Edit: Here is an example of what we would do if we had a user who logged in with their Esri credentials:
var tokenProps = {
server: "https://www.arcgis.com/sharing/rest/oauth2/authorize", // Instead point this to our IdentityProvider?
userId: "",
token: token, // Instead use our token?
ssl: true,
expires: 7200
}
IdentityManager.registerToken(tokenProps)
const map = new Map({ basemap: "streets-night-vector" })
const trailheadsLayer = new FeatureLayer({
url: `https://services1.arcgis.com/OHAG7qgFBy3zKabU/arcgis/rest/services/COVID_Trends/FeatureServer`,
renderer: new SimpleRenderer({
symbol: new PictureMarkerSymbol({
url: "http://static.arcgis.com/images/Symbols/NPS/npsPictograph_0231b.png",
width: "18px",
height: "18px"
})
}),
labelingInfo: [
new LabelClass({
labelPlacement: "above-center",
labelExpressionInfo: {
expression: "$feature.TRL_NAME"
},
symbol: new TextSymbol({
color: "#fff",
haloColor: "#5e8d74",
haloSize: "2px",
font: {
size: "12px",
family: "Noto Sans",
style: "italic",
weight: "normal"
}
})
})
]
})
map.add(trailheadsLayer)
new MapView({
center: [-118.805, 34.007],
container: mapId,
map,
zoom: 13
})
However, we need to use the token from our Identity Provider. How can this be accomplished? We have tried using IdentityManager.registerToken(tokenProps) where token props contains our token and server=identityprovider.novotx.dev but this does not result in us by passing the login popup once the map using the FeatureLayer is loaded. However it does not throw any errors visible in the dev console either.
To clarify, my question is not how to send a bearer token to ArcGIS but specifically how to exchange a token from our internal Identity Provider with either a resource directly, or for an Esri/ArcGIS access token. This must be possible because, as shown in the documentation above, a user can gain access to ArcGIS online via our internal Identity Provider.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
Hi !
Same use case here. So far we are redirecting the user a second time to get an ArcGIS token. No need to enter credentials a second time thanks to SSO but still there an additional redirection at startup which is not ideal.
Did you find a solution? I guess it would require to somehow automating the OIDC login of ArcGIS enterprise via REST call.
Thanks