- Home
- :
- All Communities
- :
- Products
- :
- ArcGIS Enterprise
- :
- ArcGIS Enterprise Questions
- :
- typical/standard/proper/expected DMZ architecture?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
typical/standard/proper/expected DMZ architecture?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm in the process of migrating a pre-10.5 "just ArcGIS Server" -type architecture to a "full-stack" of AGE.
I could use some input from any "network architecture" gurus reading this (including just plain GIS folk who happen to have such knowledge from their own implementations), as I'll eventually need to communicate some sort of plan to our network crew.
Essentially, is there a "standard" way to "communicate" AGE's best-practice/recommended DMZ requirements? Granted that different orgs might have want/need to go above/beyond depending on own security requirements, but I'm just considering the "typical" install practices. I'm sort of trying to learn what "lingo" I might need to best specify things for our networking staff.
Or,.. Is the drawing below representative of the typical/proper/expected way of setting things up for both internal/external access to the portal?... functionally complete?.. anything missing?... do something else entirely?
Thanks!
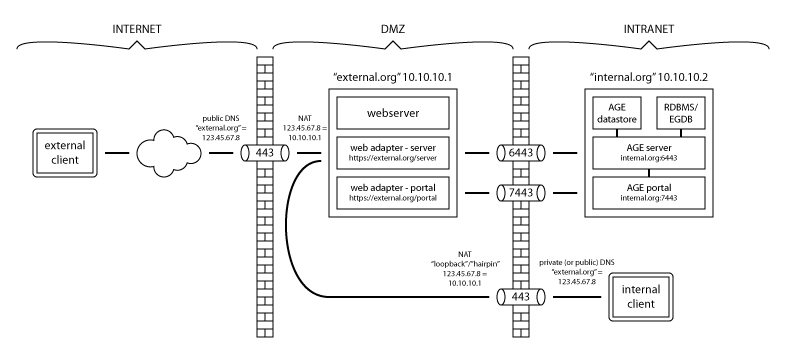
(some things simplified: http:80 traffic not shown (nor AGE's 6080/7080), "external.org" might really be "subdomain.internal.org", "internal.org" may represent >1 server, etc - but hopefully doesn't matter, it's still conceptually "equivalent enough" to our plan to be relevant, mainly the DMZ/firewall portion is the intended focus of the question)