- Home
- :
- All Communities
- :
- Products
- :
- ArcGIS Online
- :
- ArcGIS Online Ideas
- :
- Authorize users based on enterprise login attribut...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Follow this Idea
- Printer Friendly Page
- Report Inappropriate Content
Authorize users based on enterprise login attributes (SAML)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As an organization administrator, I want to control user authorization (type, role, licensing, etc.) in ArcGIS Online via SAML so that I do not need to script changes to accounts in the system. This would allow organizations using enterprise logins to let new members into the system and be selective about what the user is authorized to do at their first login and at subsequent logins.
SAML identity providers (IdPs) allow users to login who may not be licensed for access to ArcGIS Online, Pro, etc. The IdP handles authentication, the service provider (SP) handles authorization. ArcGIS Online (the SP) supports letting anyone authenticated by the IdP into the system, and supports new member defaults, but someone allowed in by the IdP may not be eligible for the defaults. In the future, someone who was eligible for access may lose that eligibility, but is still able to login through the IdP and ArcGIS Online/the SP should not allow them continued access.
For our university, alumni are able to authenticate using our IdP, but should have restricted or zero access to the ArcGIS Online organization. Former employees can login to view pay history, W-2s, etc., but should not be able to use ArcGIS Online, keep their ArcGIS Pro entitlement, etc.
Instead, the logic behind who should be allowed access, and how much access, can happen on the IdP side. The IdP can return one or more attributes describing the access the user should receive. ArcGIS Online could then allocate/deallocate/assign as needed. For instance, a custom attribute arcgisOnlineAccess might have the value "somecustomprofile." If the organization administrators have defined "somecustomprofile" to have a user type, role, Esri Access, default credits, and a set of licenses/add-ons/bundles, the user account would receive those. A "none" profile could be used to prevent use, a "limited" profile could be setup to grant some privileges, and so on. It would be up to the organization administrators to work with their IT staff to have their IdP provide the proper attribute and values, and to configure their ArcGIS Online organization with defaults.
How would this proposal affect you? It might make your user management experience that much easier.
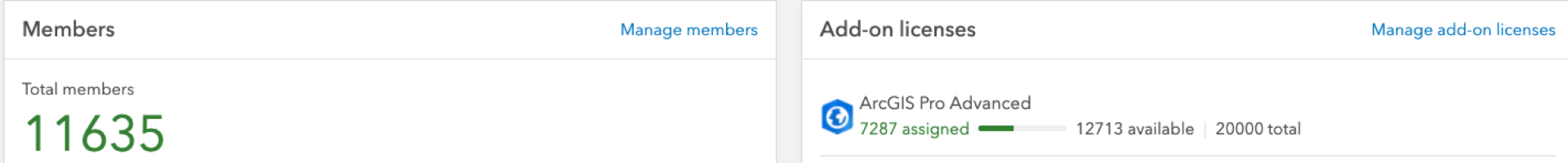
How would this affect us? The same way. Right now, our university runs a set of scripts (ArcGIS Python API) to determine what new users in ArcGIS Online should have access to, based on queries against our central directory, along with nightly updates to revoke or reauthorize users who aren't need, based on directory lookups. We lookup over 11,000 users every day, regardless of when they last logged in. This might be sufficient, but the code is somewhat fragile as ArcGIS Online quarterly updates continue to introduce changes that require fixes to our custom codebase, e.g. bundles weren't supported by our code. The logic behind authorization could be moved to our central directory and IdP, and the meaning of the attributes could be handled by the SP (ArcGIS Online). This would make the management of our >11,000 users (only about 7,300 eligible for ongoing access) easier.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.