- Home
- :
- All Communities
- :
- Products
- :
- ArcGIS Enterprise
- :
- ArcGIS Enterprise Questions
- :
- Re: SSL/TLS certificates in a fresh ArcGIS Enterpr...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SSL/TLS certificates in a fresh ArcGIS Enterprise Builder install
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello all,
After doing a base installation of ArcGIS Enterprise using Enterprise Builder 10.7.1 I notice the WebAdaptors are nicely using the domain certificate I configured in IIS. However I also noticed that the ArcGIS Server, Data Store, and Portal are using self-signed certificates (a different one each).
My initial question is if this is expected after an Enterprise Builder installation or have I gone wrong somewhere?
And then, if this is expected, is the best practice to reconfigure the Server, Portal, and Data Store to use the domain certificate? Or is there a reason to not reconfigure all 3?
Thank you in advance for any advice.
Kind regards,
Ben
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @JonathanQuinn and @BenO_Connor ,
This is fantastic information - thank you so much! I know the posts are 4 years old but they are helping me out.
I have a novice IT question - if I have 1 CA-signed Certificate from a past ArcGIS Server installation - can I use the 1 CA-signed certificate for all 4 of those locations - web adaptors, Portal, Server, and Data Store? (or do I have to get 4 different CA-signed certificates?).
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also install Root and any Intermediate certificates that come from you CA signing authority in each of your GIS Enterprise software components.
Authorities like Go-Daddy use secondary signatories to do the work for them and if the Intermediate certificates containing the secondary signatures aren't installed into the chain, Trust won't be granted (in some instances but not all).
We have also found that ArcGIS Enterprise components have real problems ingesting Go-Daddy IIS formatted certs (.p7b) that come standard in Go-Daddy Microsoft certificate downloads.
To work around the .p7b problem in a MS server house running IIS our method for implementing certs:
- Install Root and Intermediate certs to the IIS Server machine using Microsoft Windows formatted certificates from the signatory.
- Install the .PFX on any web servers hosting Web Adaptors and any Gateway machines and configure HTTPS bindings in the web servers.
- Install Root and Intermediate to each Microsoft Server Machine OS on which the GIS Enterprise components are installed using the Microsoft Windows formatted certificates.
- Switch to the Linux formatted certificate package.
- Install Linux versions of Root, Intermediate, and PFX to each ESRI Enterprise software component that requires certs. Datastore only gets a .pfx.
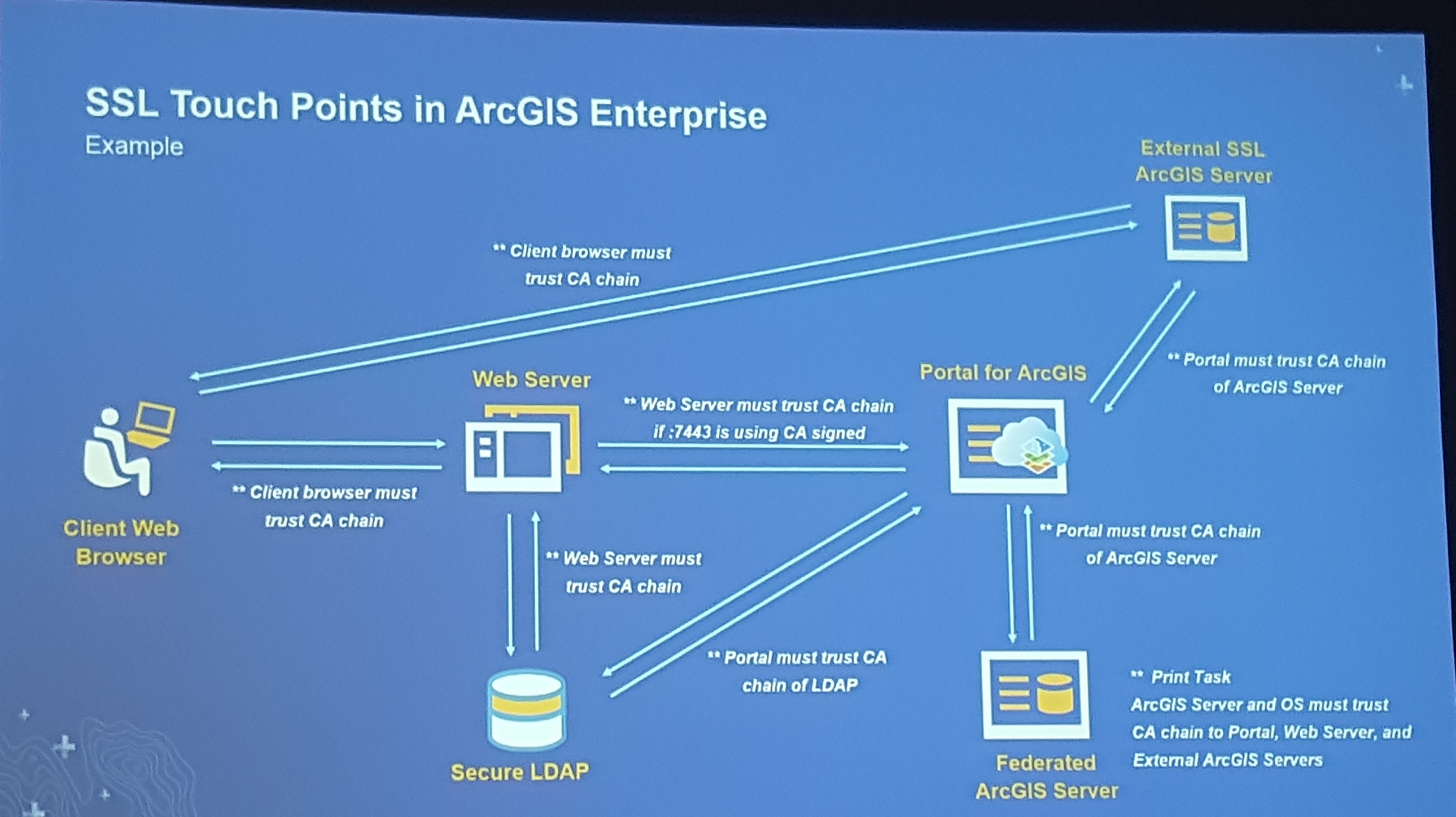
Note in the diagram below from the 2019 ESRI UC that specific trust is required in any federated configuration. Switching to all Linux versions of the certificates used inside the ESRI software components themselves completely cleared up the SSL trust problems we'd been experiencing intermittently over several versions of the GIS Enterprise.
- « Previous
-
- 1
- 2
- Next »
- « Previous
-
- 1
- 2
- Next »